There have been a lot of strange twists and turns when it comes to ransomware this month. First, we had Popcorn Time that gave you the option of screwing over people by infecting them to possibly get a free decryption key. Now, we have a new in-development variant of the Koolova Ransomware that will decrypt your files for free if you educate yourself about ransomware by reading two articles.
Discovered by security researcher Michael Gillespie, this in-development ransomware is not ready for prime time. In fact, I had to mess with it a bit and setup a local http server to even get it to display the ransom screen.
In its functional state, Koolova will encrypt a victim's files and then display a screen similar to the Jigsaw Ransomware where the text is slowly shown on the screen. This text will tell the victim that they must read two articles before they can get a decryption key, It then tells you that if you are too lazy to read two articles before the countdown gets to zero, like Jigsaw, it will delete the encrypted files. This is not an idle threat as actually does delete the files.
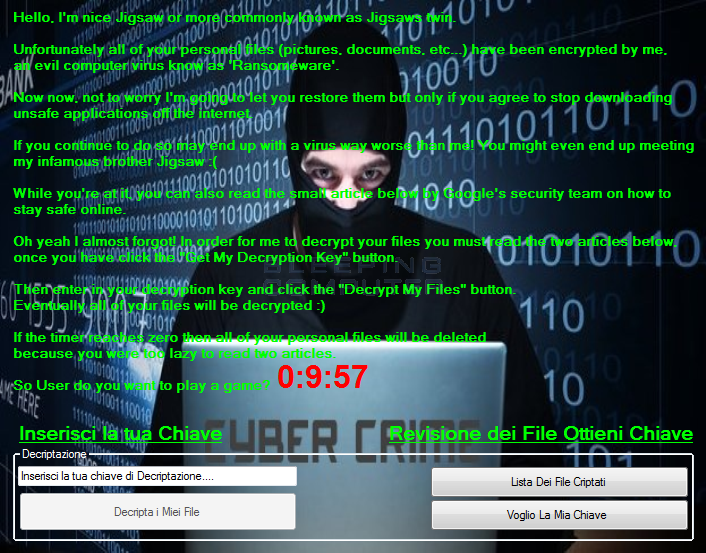
The articles that Koolova wants you to read are an article from Google Security Blog called Stay safe while browsing and BleepingComputer's very own Jigsaw Ransomware Decrypted: Will delete your files until you pay the Ransom article. Once you read both articles, the Decripta i Miei File, or Decrypt My Files, button becomes available.
Once you click on this button, Koolova will connect to the Command & Control server and retrieve the victim's decryption key. It will then display it in a message box labeled "Nice Jigsaw", in reference to the Jigsaw Ransomware, that displays your decryption key.
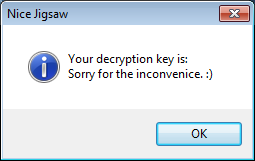
A victim will then be able to take that key and enter it into the key field in order to decrypt files.
All in all, Koolova is a very strange ransomware and one that I personally find a little creepy as it uses one of the articles I wrote as a method to gain a free decryption. As all of the Koolova ransomware variants I have seen have been in development, there is a good chance that this one will never actually make it to the wild. Then again, I have been wrong before.


Comments
DodoIso - 7 years ago
Is the encryption process very similar to jigsaw, or any other ransomware family? If so, wouldn't it be nice if the callback process be able to recover the actual private key of the evil twin ransomware as well? Just asking?
Demonslay335 - 7 years ago
@Dodolso There isn't really a "private key" for the real Jigsaw, nor is there any need for it - my decrypter handles every variant of it ever released.