A company is going around buying abandoned Chrome extensions from their original developers and converting these add-ons into adware.
This scheme came to light two days ago when the users of a popular Chrome extension began complaining about an update that requested two intrusive permissions that the extension never used, or would have never had a reason to. The two permissions are:
- Read and change data on (all) websites visited
- Manage apps, extensions, and themes
The Chrome extension in question is named Particle (formerly known as YouTube+) and is a simple tool that allows users to change the UI and behavior of some of YouTube's standard features.
Back in May, the extension's original author announced it was planning to abandon the Particle Extension and build a new one called Iridium. The original author cited an upcoming YouTube UI update that would have broken most of Particle's features, hence the reason he decided to start a new project from scratch.
Extension sold to new developer
Somewhere between May and two days ago (July 11), the original author was approached by a company that offered to buy the extension from him for a price of his choosing.
The original author says he couldn't resist this offer for an extension which he deemed abandoned, so he decided to sell. Before selling, he claims he researched the buyer before approving and says he wasn't able to find any "warning signs."
The terms of the sale also include a non-disclosure agreement that now prevents the original author from revealing the company's name.
After the Particle code had changed hands, two days ago, the new owner released a Particle update through the Chrome Web Store.
Immediately, users noticed the extension's new permissions and flocked to the original author's GitHub repo to complain about the update, only to discover that the extension changed devs without any warning to existing users.
Extension pumped with code to inject ads into websites
An analysis of the Particle source reveals that the new owner added a folder named "algoad" to the original extension's code.
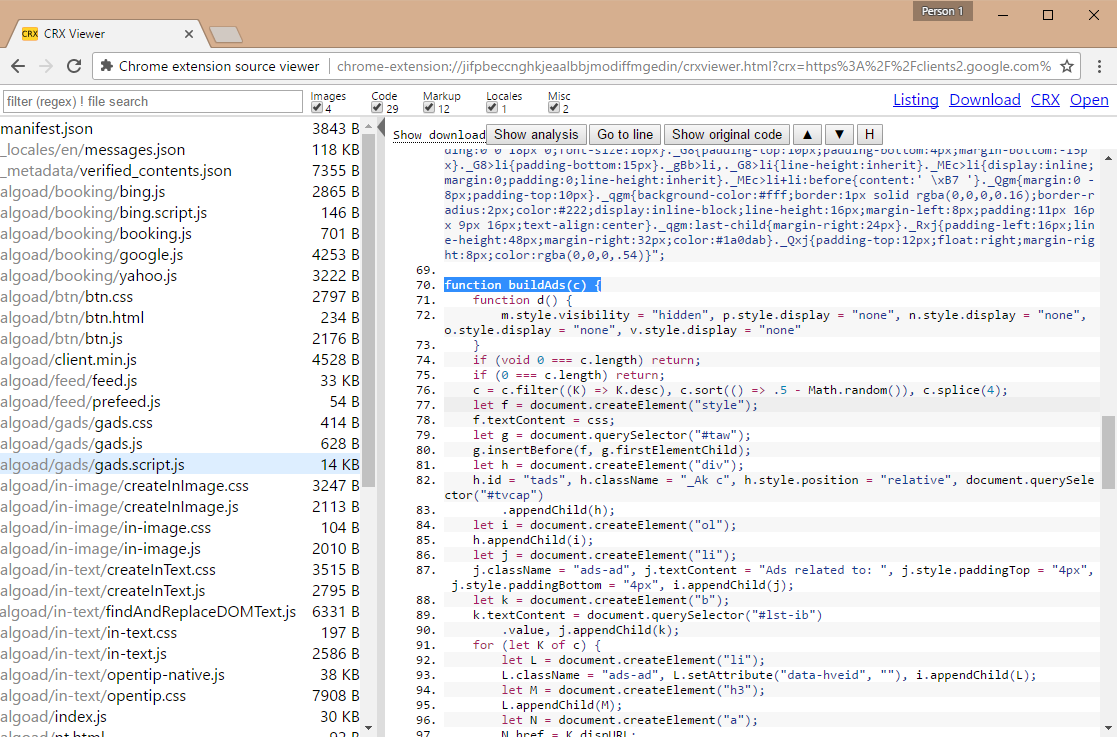
This new code injects ads in websites such as Google, Yahoo, Bing, Amazon, eBay, and Booking.com. Both Bleeping Computer and Particle users who analyzed the code saw the same malicious behavior. Bleeping Computer also asked two security researchers from Emsisoft to analyze the extension's code, and both confirmed the initial assessment.
New extension owner linked to similar adware-like extensions
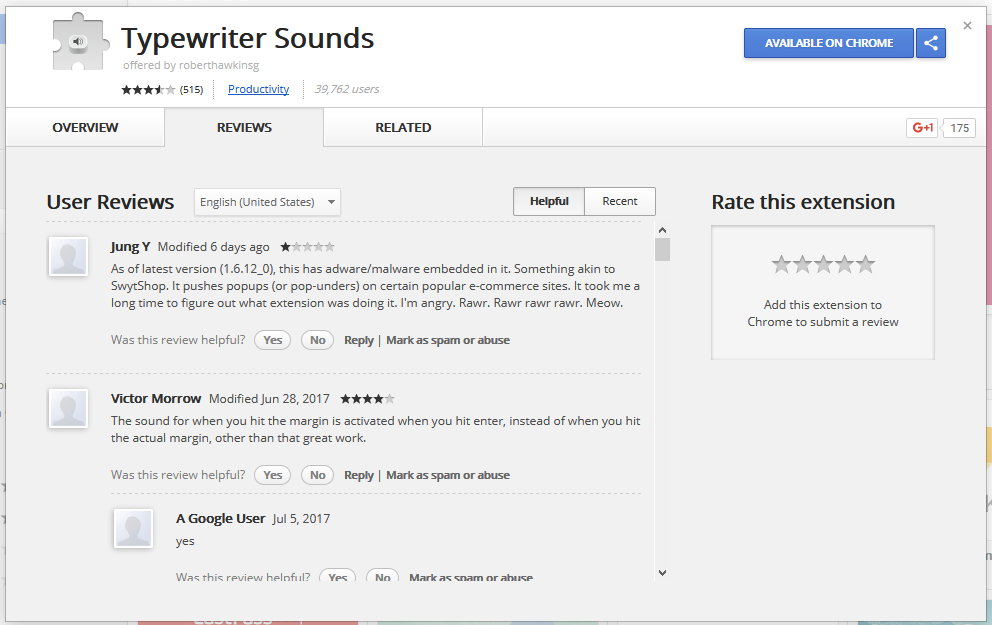
The extension's new user — roberthawkinsg — is also the author of two other Chrome extensions: "Typewriter Sounds" and "Twitch Mini Player."
Visiting the Reviews section of all these extensions we find the same complaints about how a formerly harmless add-on turned into adware.
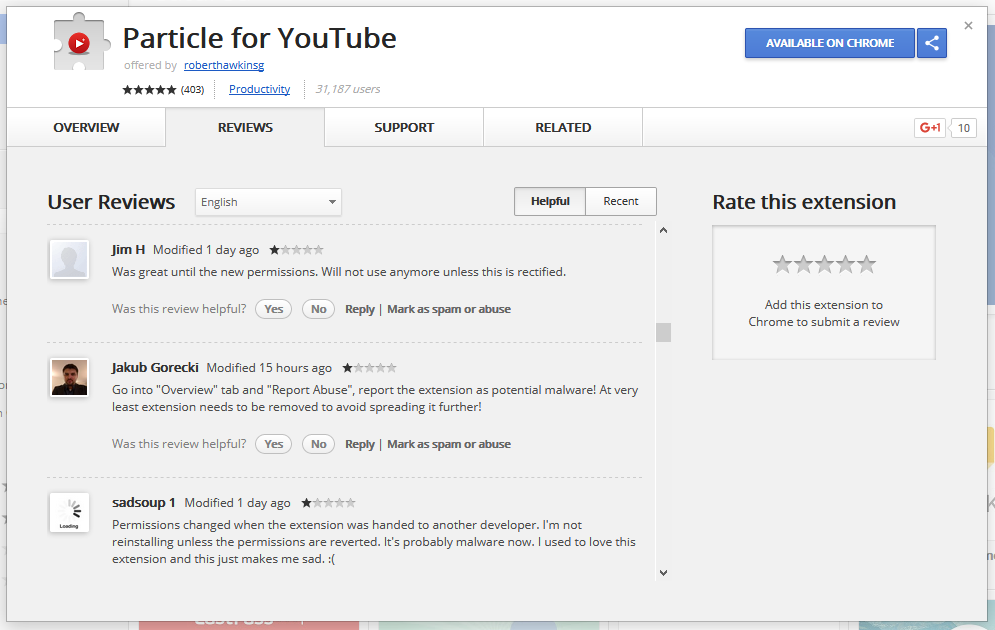 |
 |
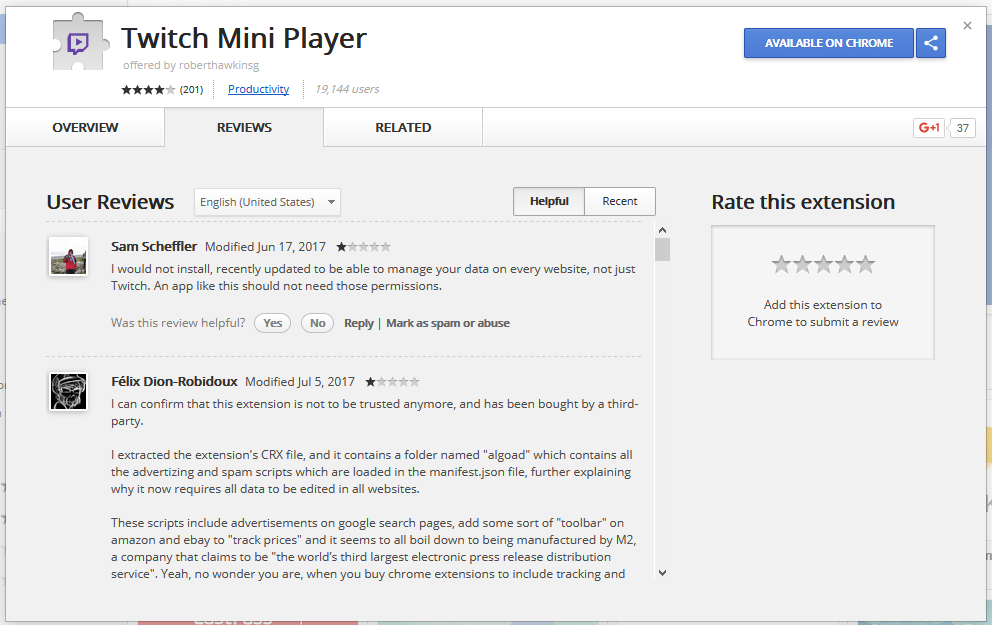 |
At the time of writing the Particle extension has just over 31,000 users, the Typewriter Sounds extension has nearly 40,000 users, and the Twitch Mini Player extension has nearly 20,000 users.
In the meantime, the original author of the Particle Chrome extension is recommending that users install a Userscript version of the Particle extension, or wait until the new Iridium extension is released.


Comments
Lawrence Abrams - 6 years ago
Malicious chrome extensions are running rampant. Ad injecting is actually not that common. Mostly see search hijacks. Won't be surprised if Google bans this extension soon.
quodroc - 6 years ago
This is not a new phenomenon, it has been a problem for years (for example, see https://www.reddit.com/r/IAmA/comments/1vjj51/i_am_one_of_the_developers_of_a_popular_chrome/ )
Every extension developer with a decent amount of users is regularly spammed by these adware companies trying to buy the extension.
GT500 - 6 years ago
For those who used YouTube+/Particle, and want to keep up with Iridium releases to see when there's an extension available for their browser, here's a link to a feed for the releases:
https://github.com/ParticleCore/Iridium/releases.atom
BTW: Anyone know of a good RSS/Atom extension for Google Chrome? I've been using feeder, and I don't particularly like it...
Ryaniskira - 6 years ago
Odd, I've been using Youtube+ via Tampermonkey for a long while now, didn't even know it had a Chrome extension.
freshcheddar - 6 years ago
Thanks for the article. I wondered where that app went. Now happy with the old Youtube adn the TamperMonkey Script version.
atheoang3l0 - 6 years ago
Seriously? Luckily, I was using the script version. I didn't even know it was in the CWS. IIRC, its alpha/beta didn't have a browser extension version. I'm now using FF and I hope its add-ons aren't sellable.