.jpg)
Ongoing phishing campaigns use the recent coronavirus outbreak as bait in attacks targeting individuals from the United States and the United Kingdom, impersonating the US CDC and virologists, warning of new infection cases in their area, and providing 'safety measures.'
The global scale health crisis triggered by infections with the new 2019 novel coronavirus (also known as 2019-nCOV and Wuhan coronavirus) is exploited by the attackers for their own malicious purposes.
The World Health Organization (WHO) said on January 30, 2020, that the 2019 novel coronavirus outbreak is a public health emergency of international concern, while U.S. Health and Human Services Secretary Alex M. Azar on Friday also declared it a "public health emergency for the entire United States."
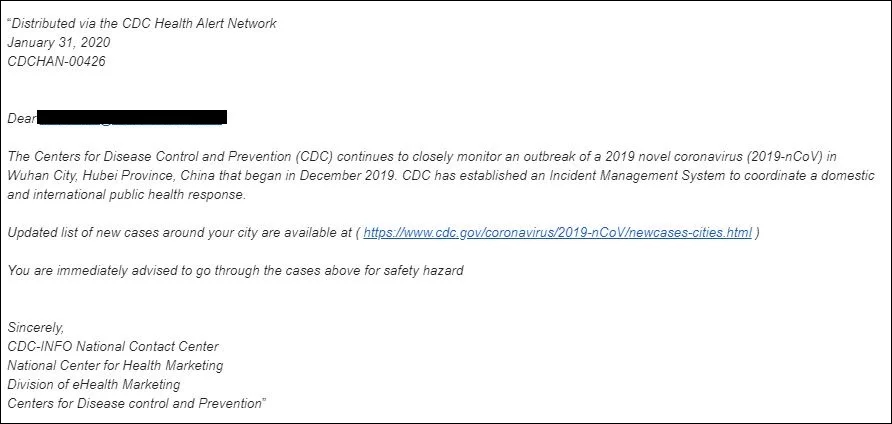
Wuhan coronavirus phishing campaign #1
In the phishing campaign spotted by researchers at phishing simulation and security awareness training outfit KnowBe4, the attackers promise to provide a list of active infections in the surrounding area to trick their potential victims into clicking a link embedded in the message and leading to a credential phishing page.
In a sample phishing email spotted by KnowBe4, the attackers try to pass their spam as an official alert message distributed via the CDC Health Alert Network.
The targets are then informed that the "CDC has established an Incident Management System to coordinate a domestic and international public health response."
The phishers then throw in their lure, in the form of a link promising to provide the recipient with an updated list of new cases of infection around their city.
"You are immediately advised to go through the cases above for safety hazard," the attackers add, trying to induce a sense of urgency that would trick the target into acting on instinct and not think about the potential dangers ahead.
The link is camouflaged as a link to the official CDC website and it is used to redirect the victims to an attacker-controlled and Outlook-themed phishing landing page used for collecting and stealing user credentials.
KnowBe4 CEO Stu Sjouwerman told Bleepingcomputer that these emails were spotted on Friday afternoon. "We expect a variety of campaigns with different payloads to arrive shortly, Emotet has already been seen using this same social engineering tactic in Japan, leveraging the Coronavirus."
"This phish leverages public fear over a widely publicized virus threat," Eric Howes, principal researcher at KnowBe4 also told us.
"It is a bit unusual in that the bad guys are usually not so nimble in exploiting current events (they seem to put more time/effort in developing payloads and methods for obfuscating payloads). Then again, this story has been building for several weeks.
The phishing email itself is rather well done, so I'm guessing whoever is behind it modeled the email after existing CDC press releases.
There is a subject/verb agreement error in the second paragraph, but it's a common one that plenty of folks make. Still, not the kind of error one would expect from a professional PR operation, which the CDC undoubtedly has. Doubtful whether most readers would notice, though."
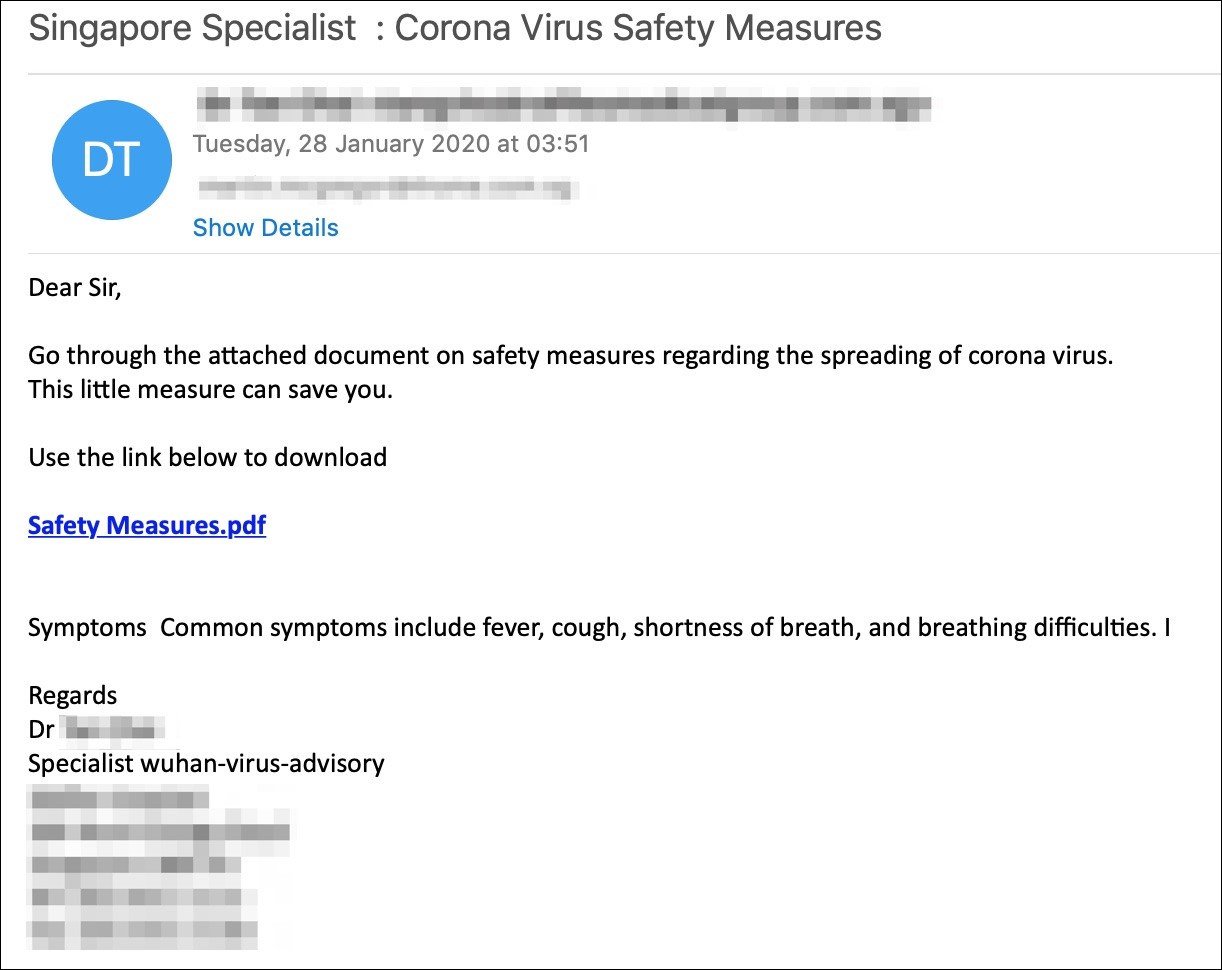
2019-nCOV phishing campaign #2
Another phishing campaign using Wuhan coronavirus lures to target both US and UK individuals was detected by security firm Mimecast.
These series of phishing emails ask the recipients to "go through the attached document on safety measures regarding the spreading of coronavirus."
"This little measures can save you," also add the attackers, then urging the targets to download a malicious PDF designed to infect their computers with a malware payload.
"The sole intention of these threat actors is to play on the public’s genuine fear to increase the likelihood of users clicking on an attachment or link delivered in a malicious communication, to cause infection, or for monetary gain," explained Francis Gaffney, Mimecast's director of threat intelligence.
"This is a rational choice by criminals as research has shown that over 90% of compromises occur by email, and that over 90% of those breaches are primarily attributable to user error."
Mimecast recommends taking at least the following basic measures to defend against such attacks:
• Be vigilant to email communications in relation to staying safe and protected from the coronavirus
• Implement reliable cybersecurity solutions across their technology, such as antivirus solutions
• Adopt cyber hygiene practices, such as using strong passwords use and never enabling attachment macros
Coronavirus public health emergency used to push Emotet
The coronavirus outbreak is also used as bait by an active malspam campaign distributing Emotet payloads via emails that alert of coronavirus infection reports in several Japanese prefectures, including Gifu, Osaka, and Tottori.
Just as the actors behind the phishing campaigns spotted by Mimecast and KnowBe4, the Emotet gang is also known for taking advantage of trending currents events and approaching holidays.
The take advantage of such occasions to send out targeted custom templates to their victims, as was the case before a Greta Thunberg Demonstration or when the 2019 Christmas and Halloween parties were closing in.
"This new approach to delivering Emotet may be significantly more successful, due to the wide impact of the coronavirus and the fear of infection surrounding it," IBM's X-Force Threat Intelligence researchers said.


Comments
Some-Other-Guy - 4 years ago
Coronavirus will now be imported in Chinese Exports
Stopping only "People" will not stop the Virus
BUY AMERICAN!
Nevermind......Too Late!
buddy215 - 4 years ago
Possibly...no one knows for how long this virus can survive outside of a host....on surfaces.
Some-Other-Guy - 4 years ago
Probably not more than a few hundred thousand years
Maybe when Winter is over, we could freeze it and find out
https://nypost.com/2020/01/23/15000-year-old-viruses-found-trapped-in-tibetan-glacier/