
A ransomware group has now started to run Facebook advertisements to pressure victims to pay a ransom.
When modern ransomware was first introduced in 2012, we saw a new extortion attack where threat actors extort victims by encrypting their files and then demand a ransom to get a decryptor.
In November 2019, a new double-extortion strategy was adopted by ransomware gangs that involve hackers also stealing unencrypted files before encrypting devices. The attackers then threaten to release these stolen files on ransomware data leak sites if a ransom is not paid.
Since then, ransomware gangs have become media savvy, where they have post press releases or contact journalists to share their latest exploits to exert pressure on victims.
Ragnar Locker takes out Facebook ads
Yesterday, the ransomware operators behind Ragnar Locker took it to the next level by hacking into a Facebook advertiser's account and creating advertisements promoting their attack on Campari Group.
Last week, Italian liquor company Campari Group suffered a Ragnar Locker ransomware attack where the attackers claim to have stolen 2 TB of unencrypted files before encrypting their network. To recover their files, the hackers demanded a $15 million ransom.
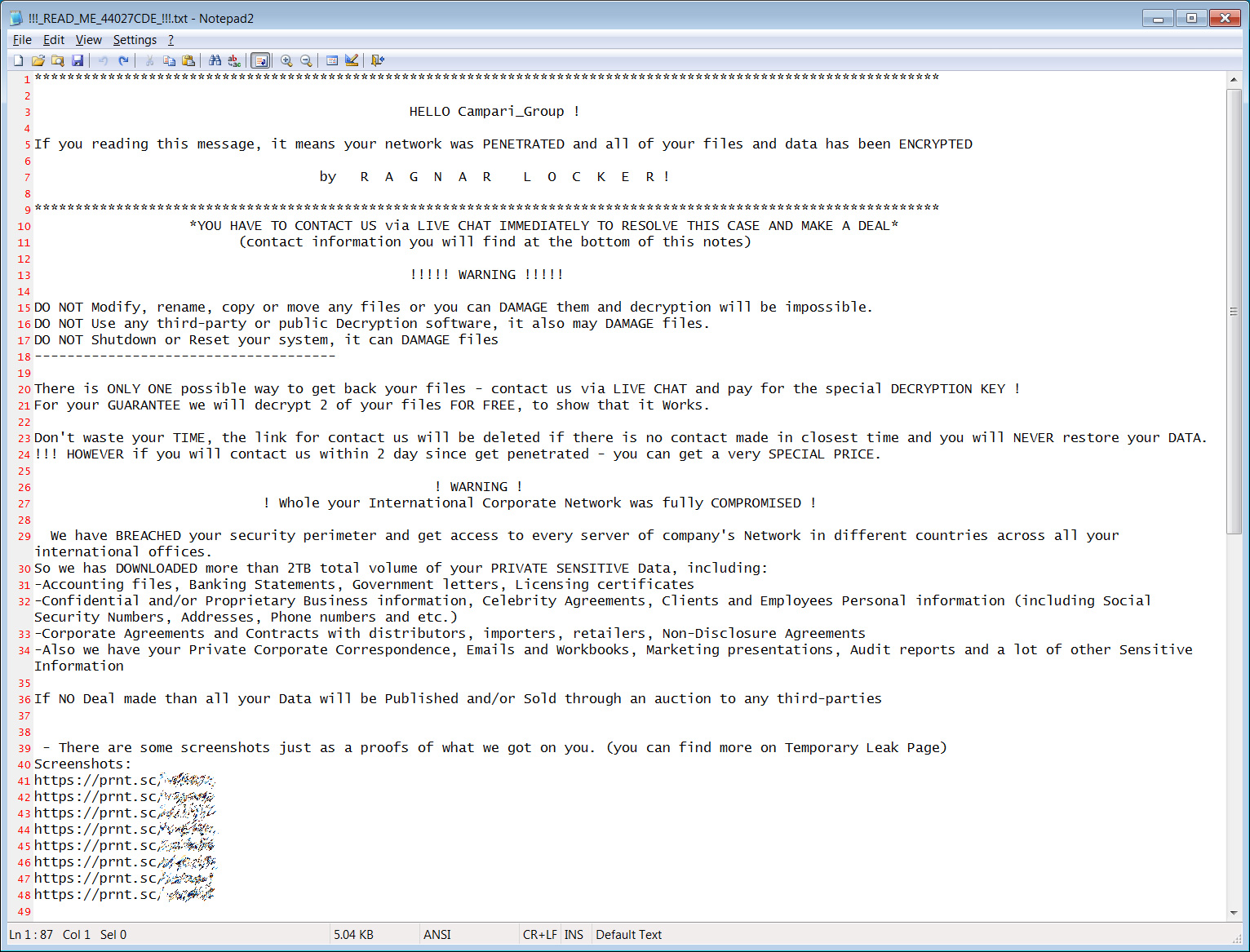
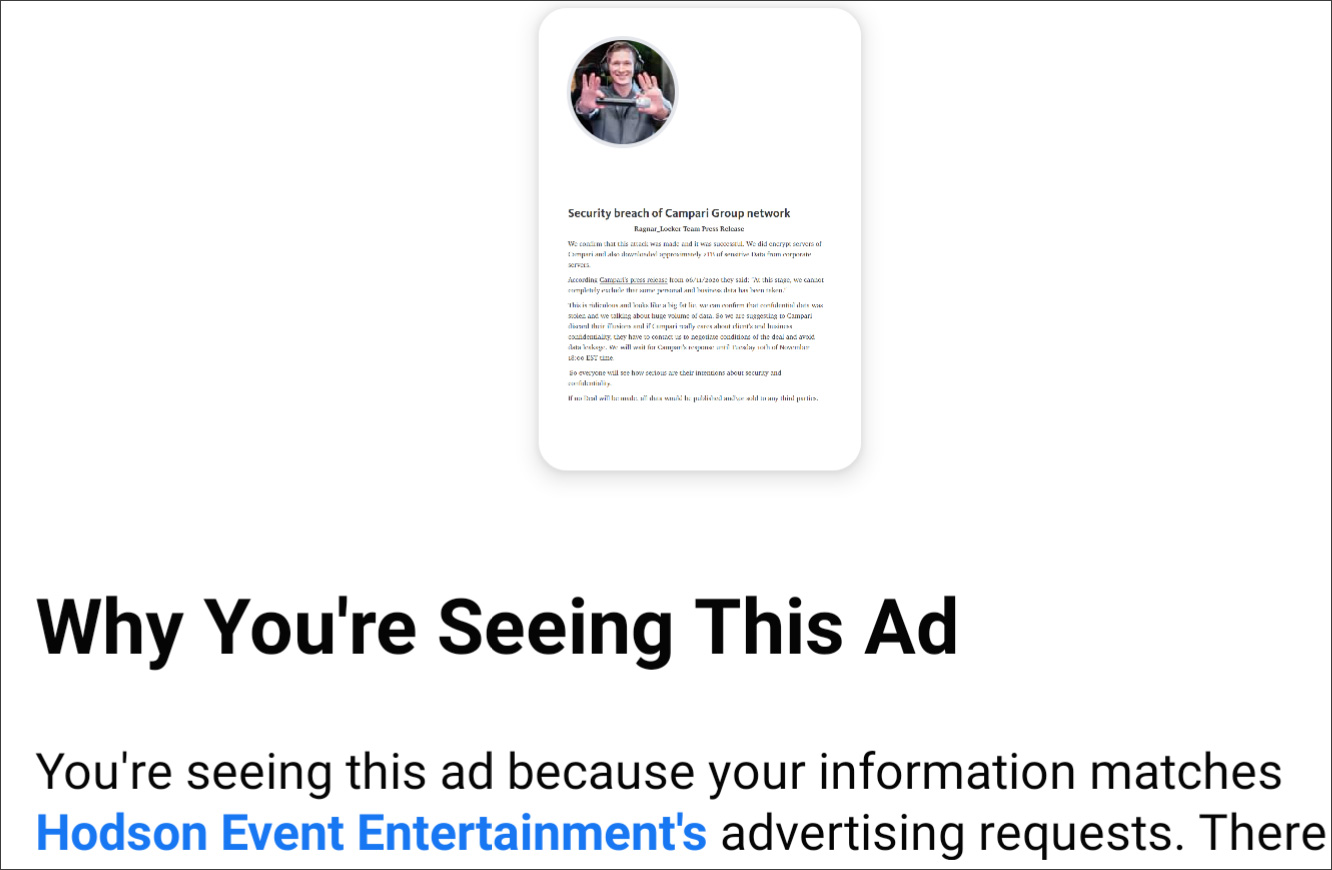
As first reported by Brian Krebs, the Ragnar Locker gang hacked into a Facebook account to run advertisements warning Campari that their data would be published if they do not pay the ransom.
This Facebook advertisement was titled "Security breach of Campari Group network" by the "Ragnar_Locker Team" and warned that further sensitive data would be released.
Source: Krebsonsecurity.com
Chris Hodson, the hacked Facebook account owner, told Brian Krebs that the advertisement was shown to over 7,000 Facebook users before Facebook detected it as a fraudulent campaign.
Ransomware actors have long threatened to escalate their extortion attempts by contacting stock exchanges, major media, and clients about a victim's attacks and loss of data.
This new tactic of promoting attacks through Facebook shows the continuing evolution of ransomware extortion. With ransom demands and payments in the tens of millions, we can expect to see further escalations in the future.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now