
Microsoft today shared tips on how to defend against human-operated ransomware attacks known to be behind hundreds of millions of dollars in losses following campaigns targeting enterprises and government entities.
Ransomware families such as Sodinokibi (REvil), Samas, Bitpaymer, DoppelPaymer, Dharma, and Ryuk are deployed by human operators, which makes these attacks a lot more dangerous than auto-spreading ransomware like NotPetya, WannaCry, or those installed via malware and phishing attacks.
This is because the actors that manually infiltrate an organization's IT infrastructure can adapt to the challenges posed by security defenses and can use a variety of techniques to further infiltrate the targeted environments using techniques such as privilege escalation and credential dumping.
"They exhibit extensive knowledge of systems administration and common network security misconfigurations, perform thorough reconnaissance, and adapt to what they discover in a compromised network," the Microsoft Defender Advanced Threat Protection (ATP) Research Team says.
"They take advantage of similar security weaknesses, highlighting a few key lessons in security, notably that these attacks are often preventable and detectable."
Microsoft shared information on the different entrance vectors and post-exploitation methods used by the operators behind DoppelPaymer, Dharma, and Ryuk, and showed that there's an overwhelming overlap in the security misconfigurations they abuse as part of their devastating attacks.
To show the actual impact ransomware had on its victims, after analyzing collected ransomware ransom notes and cryptocurrency wallets, the FBI said at last week's RSA security conference that victims have paid more than $140 million to ransomware operators during the past six years.
Ryuk ransomware deployment techniques and tactics
Ryuk is the most dangerous ransomware family out of the three highlighted by Microsoft, with the FBI saying that its operators were able to collect over $61 million in ransoms from their victims — this total is definitely a lot larger considering that the agency did not have access to all of the Ryuk ransom notes and wallets.
This ransomware family is one of the potential malware payloads delivered onto systems infected with the Trickbot Trojan.
"At the beginning of a Ryuk infection, an existing Trickbot implant downloads a new payload, often Cobalt Strike or PowerShell Empire, and begins to move laterally across a network, activating the Trickbot infection for ransomware deployment," Microsoft explains.
Also, the operators will not immediately deploy the ransomware payload on the victims' networks after the Trickbot infections occur but they will instead wait weeks or even months after the infiltration has started.
This happens because, in a lot of cases, the targets will either completely ignore the initial Trickbot infection as it is seen as a low-priority threat and that allows them to collect a lot more data and information.
Once the attack starts, the actors will start a network surveillance process and will attempt to move laterally throughout the network using Cobalt Strike or PowerShell to collect info for credential theft.
 |
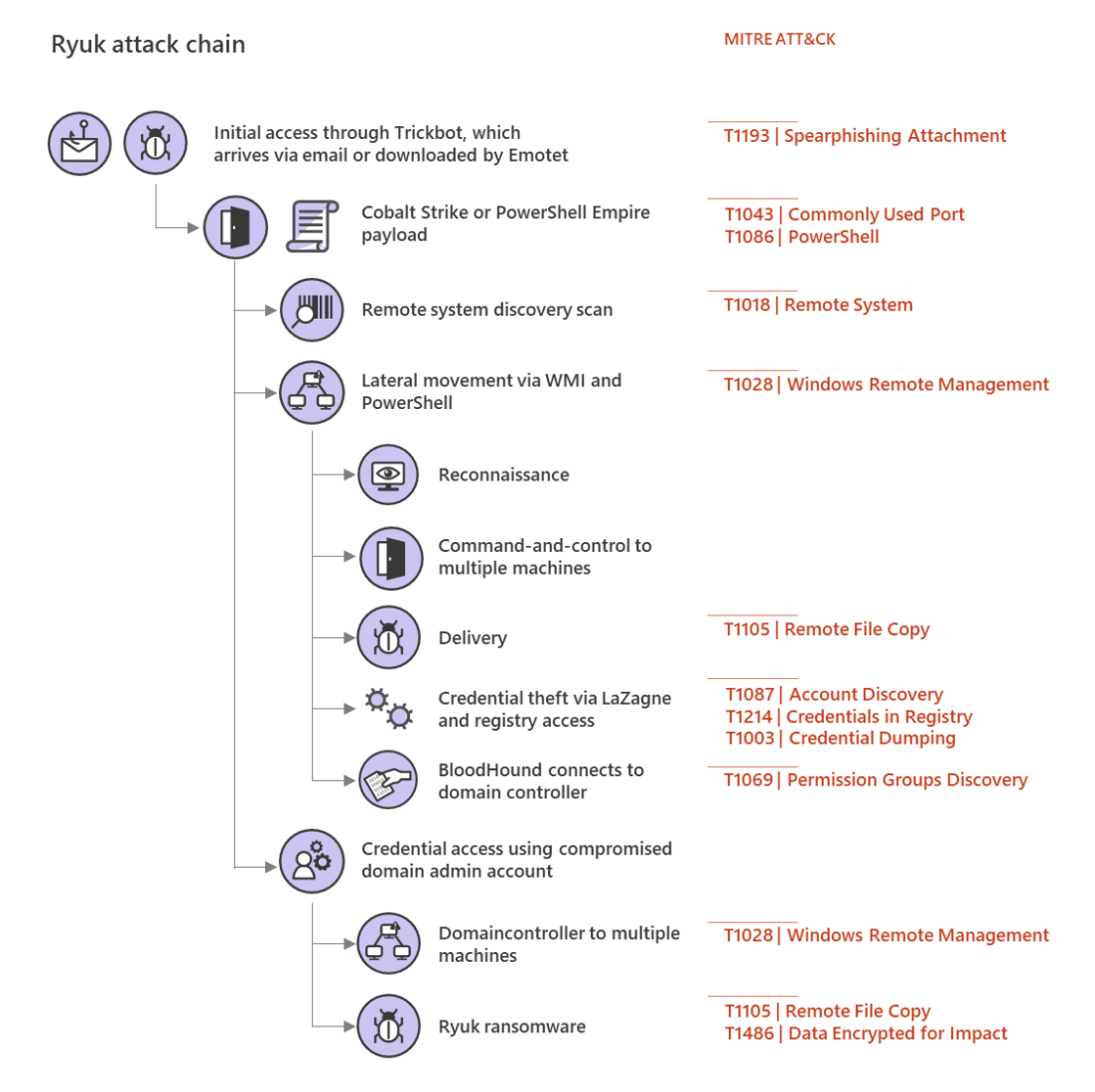 |
"The attackers then continue to move laterally to higher-value systems, inspecting and enumerating files of interest to them as they go, possibly exfiltrating this data," Microsoft adds. "The attackers then elevate to domain administrator and utilize these permissions to deploy the Ryuk payload."
"The Ryuk operators use stolen Domain Admin credentials, often from an interactive logon session on a domain controller, to distribute the Ryuk payload.
"They have been seen doing this via Group Policies, setting a startup item in the SYSVOL share, or, most commonly in recent attacks, via PsExec sessions emanating from the domain controller itself."
Dharma and DoppelPaymer TTPs
One of the groups that use Dharma ransomware in their attacks (a group tracked as PARINACOTA by Microsoft) is highly active and it has been observed by the Redmond researchers deploying the ransomware on the systems of at least three or four organizations every week.
Microsoft says that during 18 months of monitoring, PARINACOTA was observed while changing "tactics to match its needs and use compromised machines for various purposes, including cryptocurrency mining, sending spam emails, or proxying for other attacks."
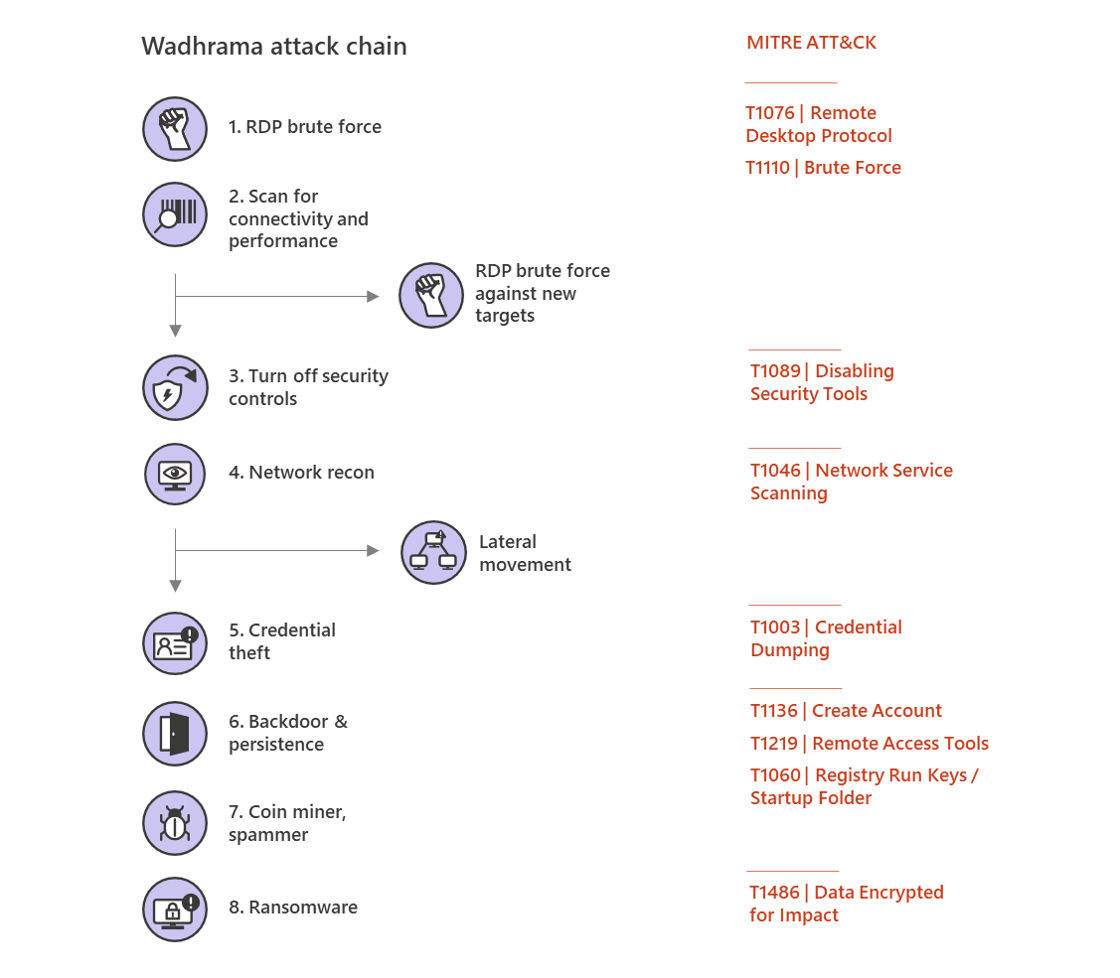
This group's operators will most commonly use brute force attacks against servers reachable over the internet via the Remote Desktop Protocol (RDP).
After it infiltrates an organization's network, they will start scanning for other RDP servers and brute force their way into those too, turning off security controls and moving laterally to other systems after a network reconnaissance stage.
They will then steal credentials to gain administrative privileges so that they can toggle off security solutions, and will start deploying backdoors for persistence, as well as coin miners and spammers to use them as part of large scale spam and illicit mining campaigns.
Only after going through all these stages and running their spam and mining operations for a few weeks, PARINACOTA will deploy the Dharma ransomware to encrypt the organizations' systems, after first deleting local backups.
 |
 |
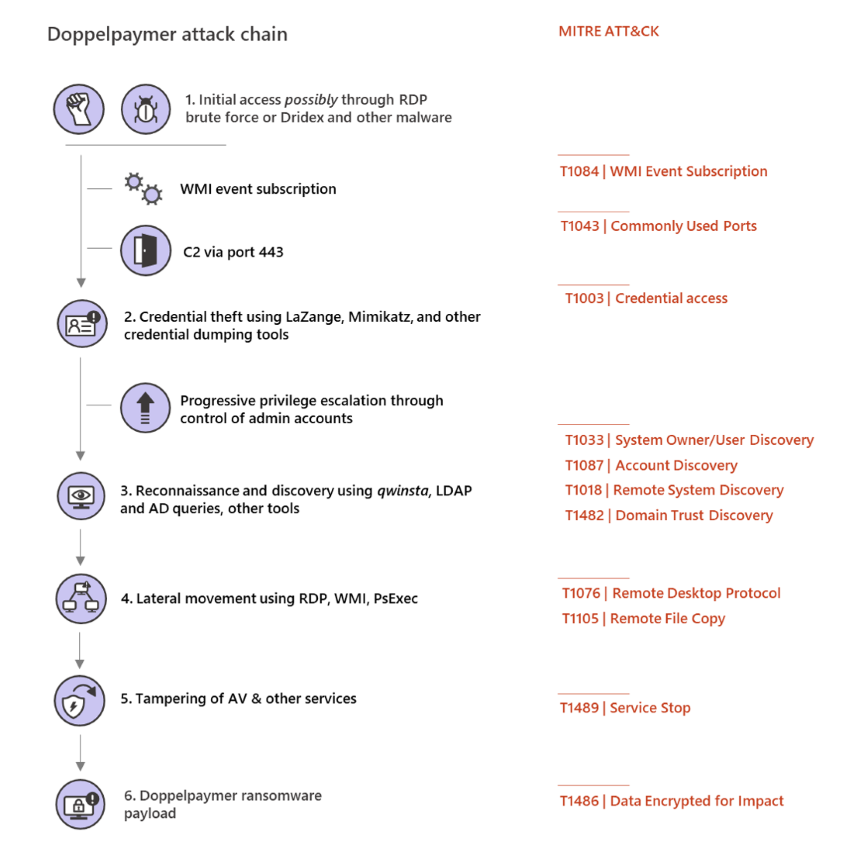
DoppelPaymer ransomware is delivered within victims' networks by its human operators using previously stolen user credentials with high privileges and tools like Group Policy and PsExec.
The operators "often abuse service accounts, including accounts used to manage security products, that have domain admin privileges to run native commands, often stopping antivirus software and other security controls," Microsoft says.
"The presence of banking Trojans like Dridex on machines compromised by DoppelPaymer point to the possibility that Dridex (or other malware) is introduced during earlier attack stages through fake updaters, malicious documents in phishing email, or even by being delivered via the Emotet botnet."
Even though Dridex is most likely as part of the infiltration process, RDP brute force artifacts have also been observed by Microsoft while monitoring the actors activities and analyzing some of the impacted networks.
The operators will also often deploy their payloads on networks previously compromised by other attackers months before the systems get encrypted with DoppelPaymer.
"The success of attacks relies on whether campaign operators manage to gain control over domain accounts with elevated privileges after establishing initial access," Microsoft adds.
This is done via credential theft attacks powered by Mimikatz, LaZange, and other credential dumping tools, and via privilege escalation by gaining control of admin accounts.
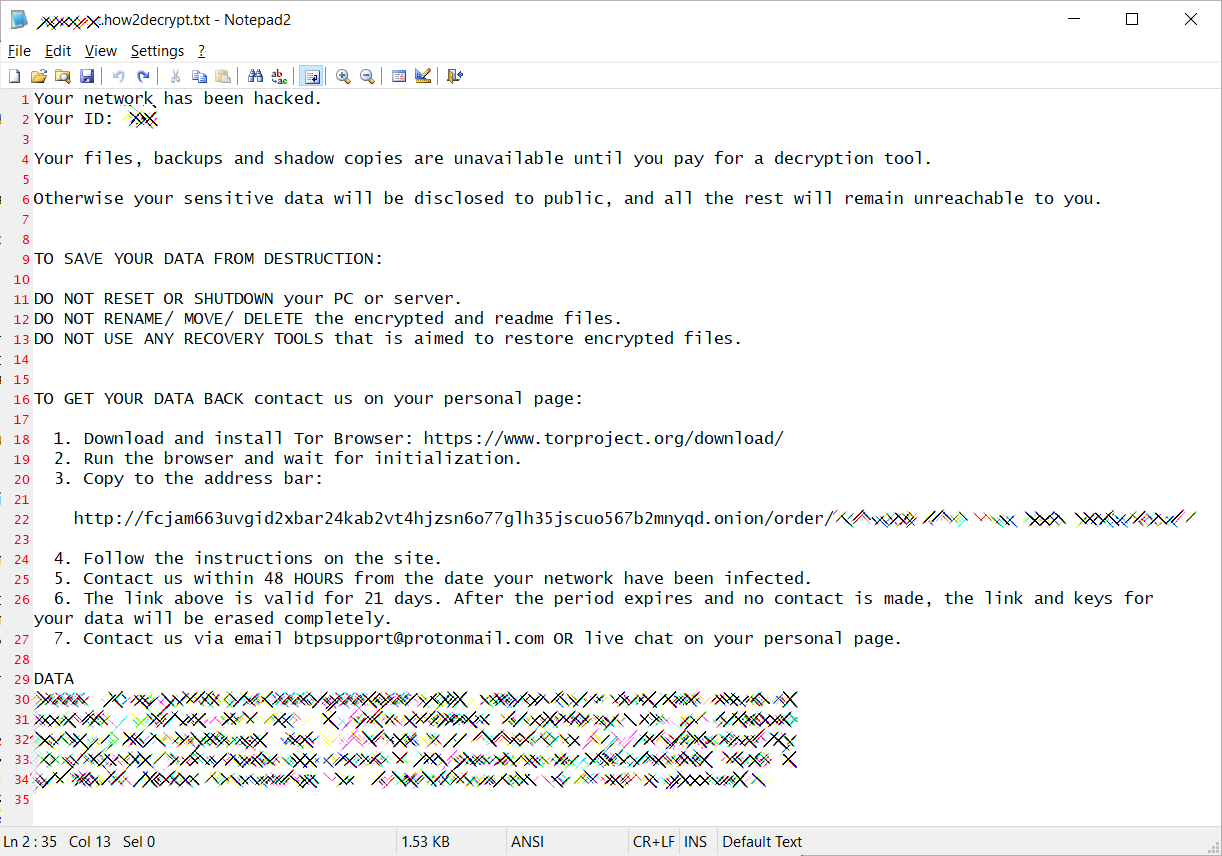 |
 |
As Microsoft notes, DoppelPaymer attacks will not encrypt all systems on compromised networks. Instead, the operators will deploy a ransomware payload on a limited subset and an even smaller set of the infected machines will have their files encrypted.
Additionally, "the attackers maintain persistence on machines that don’t have the ransomware and appear intent to use these machines to come back to networks that pay the ransom or do not perform a full incident response and recovery."
The DoppelPaymer operators have also launched a data leak site in February 2020 to be used to shame victims who don't pay the ransoms and publish files stolen from their computers before encryption.
This move is part of a new trend started by Maze Ransomware in November 2019 and later adopted by operators of other ransomware like Sodinokibi, Nemty Ransomware, and BitPyLock.
Defense measures against human-operated ransomware attacks
Microsoft advises security teams and admins at organizations that might be targeted in the future by this type of ransomware campaigns to take defensive measures designed to bock common attack techniques or at least dramatically reduce their effectiveness.
The Microsoft Defender Advanced Threat Protection (ATP) Research Team recommends implementing these mitigation measures against human-operated ransomware attacks:
• Harden internet-facing assets:
- Apply latest security updates
- Use threat and vulnerability management
- Perform regular audit remove privileged credentials
• Thoroughly investigate and remediate alerts:
- Prioritize and treat commodity malware infections as potential full compromise
• Include IT Pros in security discussions:
- Ensure collaboration among SecOps, SecAdmins, and IT admins to configure servers and other endpoints securely
• Build credential hygiene:
- Use MFA or NLA, and use strong, randomized, just-in-time local admin passwords
- Apply principle of least-privilege
• Monitor for adversarial activities:
- Hunt for brute force attempts
- Monitor for cleanup of Event logs
- Analyze logon events
• Harden infrastructure:
- Use Windows Defender Firewall
- Enable tamper protection
- Enable cloud-delivered protection
- Turn on attack surface reduction rules and AMSI for Office VBA


Comments
Nikelpede - 4 years ago
People need to use a white list for RDP access.
It's a pain in the neck to start but well worth it.
I also monitor for bad logins and block the IP of attackers.
Free tools will send you an email if you are getting attacked.
Set your account lockout to 3 tries.
I have over 1.3 Billion IP's blocked in my firewall.
Whalley_World - 4 years ago
We don't even use RDP anymore, we use SCCM for remote access instead. I like the rest.