
Unknown threat actors are using previously undetected malware to backdoor macOS devices and exfiltrate information in a highly targeted series of attacks.
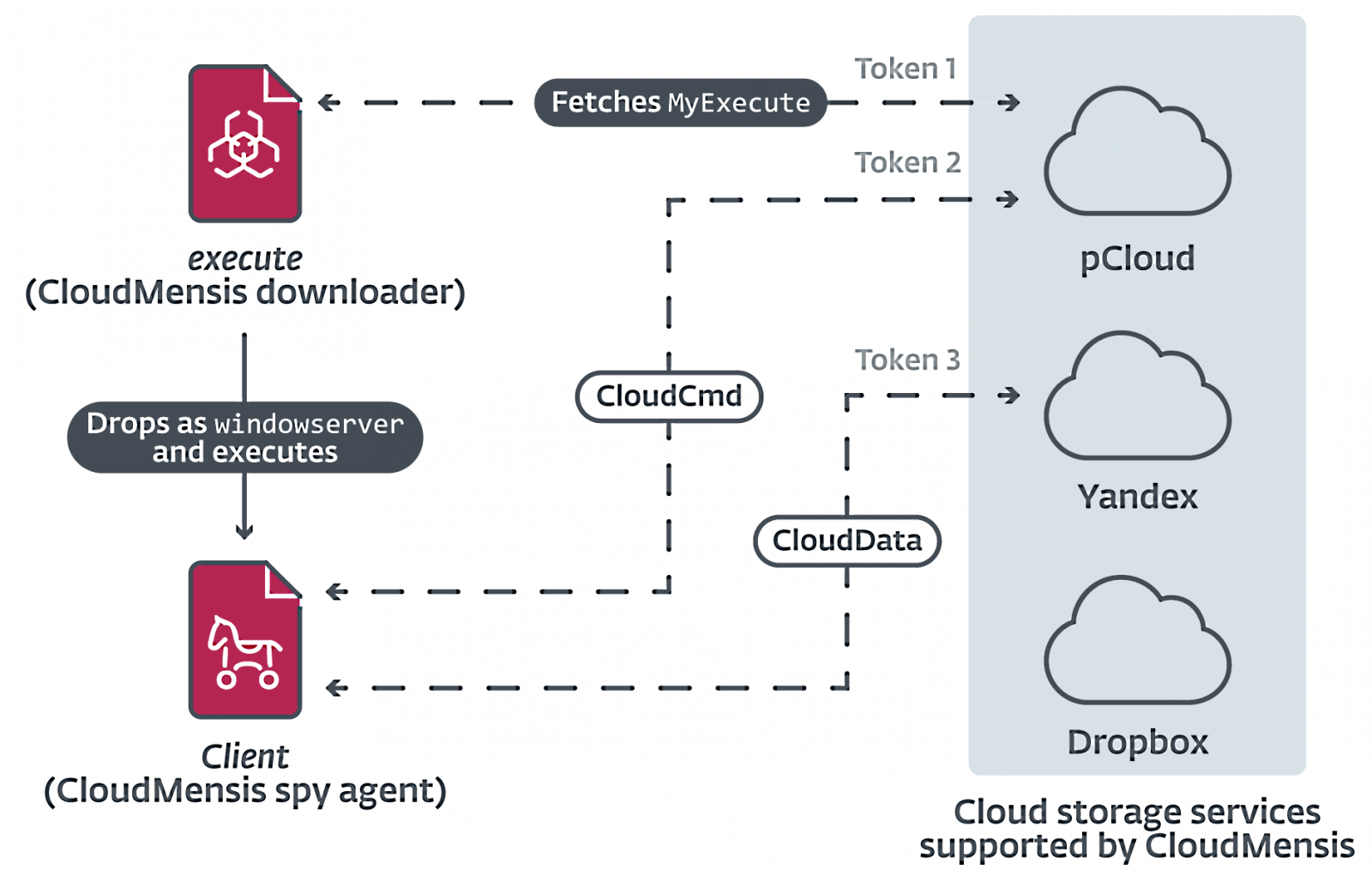
ESET researchers first spotted the new malware in April 2022 and named it CloudMensis because it uses pCloud, Yandex Disk, and Dropbox public cloud storage services for command-and-control (C2) communication.
CloudMensis' capabilities clearly show that its operators' main goal is to collect sensitive info from infected Macs through various means.
These include screenshots, exfiltration of documents and keystrokes, as well as listing email messages, attachments, and files stored from removable storage.
The malware comes with support for dozens of commands, allowing its operators to perform a long list of actions on infected Macs, including:
- Change values in the CloudMensis configuration: cloud storage providers and authentication tokens, file extensions deemed interesting, polling frequency of cloud storage, etc.
- List running processes
- Start a screen capture
- List email messages and attachments
- List files from removable storage
- Run shell commands and upload the output to cloud storage
- Download and execute arbitrary files
Based on ESET's analysis, the attackers infected the first Mac with CloudMensis on February 4, 2022. Since then, they've only sporadically used the backdoor to target and compromise other Macs, hinting at the campaign's highly targeted nature.
The infection vector is also unknown, and the attackers' Objective-C coding abilities also show they're unfamiliar with the macOS platform.
"We still do not know how CloudMensis is initially distributed and who the targets are," ESET researcher Marc-Etienne Léveillé said.
"The general quality of the code and lack of obfuscation shows the authors may not be very familiar with Mac development and are not so advanced.
"Nonetheless, a lot of resources were put into making CloudMensis a powerful spying tool and a menace to potential targets."
Bypassing privacy protections
After being deployed on a Mac, CloudMensis can also bypass the macOS Transparency Consent and Control (TCC) system, which prompts the user to grant apps permission to take screen captures or monitor keyboard events.
TCC is designed to block macOS apps from accessing sensitive user data by enabling macOS users to configure privacy settings for apps installed on their systems and devices connected to their Macs, including microphones and cameras.
The rules created by each user are saved within a database on the Mac protected by System Integrity Protection (SIP), which ensures that only the TCC daemon can modify it.
If the user disables SIP on the system, CloudMensis will grant itself permissions by adding new rules to the TCC.db file.
However, "if SIP is enabled but the Mac is running any version of macOS Catalina earlier than 10.15.6, CloudMensis will exploit a vulnerability to make the TCC daemon (tccd) load a database CloudMensis can write to."
The vulnerability it uses, in this case, is a CoreFoundation bug tracked as CVE-2020–9934 and patched by Apple two years ago.
While ESET has only seen this malware abusing this flaw in the wild, the attackers have no shortage of ways to bypass TCC, seeing that Apple has also recently addressed bugs leading to a similar impact.
For instance, they could exploit the Microsoft-discovered powerdir flaw (CVE-2021-30970), Time Machine mounts (CVE-2020-9771), environment variable poisoning (CVE-2020-9934), or a bundle conclusion issue (CVE-2021-30713).
By circumventing TCC, the malware gains access to infected Macs' screens, can scan connected removable storage for documents of interest, and log keyboard events.
"Usage of vulnerabilities to work around macOS mitigations shows that the malware operators are actively trying to maximize the success of their spying operations," ESET concluded.
"At the same time, no undisclosed vulnerabilities (zero-days) were found to be used by this group during our research. Thus, running an up-to-date Mac is recommended to avoid, at least, the mitigation bypasses."


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now